Finastra Confirms Major Data Breach, Investigates Theft of 400GB of Client Data
Finastra, a global fintech leader, confirmed a major data breach affecting its Secure File Transfer Platform. The breach, caused by stolen credentials, resulted in the theft of 400GB of sensitive data. Investigations are ongoing as the company ensures customer operations remain unaffected.

Finastra, a global leader in financial technology serving 45 of the world’s top 50 banks, has reported a significant data breach targeting its internal file transfer system. The London-based firm, which facilitates banking and wire transfers for over 8,100 financial institutions worldwide, detected the breach on November 7, 2024.
The breach has raised concerns over client data security and confidentiality, as the attackers appear to have gained access through compromised credentials.
How the Breach Happened
The attack targeted Finastra's internally hosted Secure File Transfer Platform (SFTP), a system used for managing sensitive client data. According to Finastra, the attackers exploited stolen credentials—essentially a compromised username and password—to infiltrate the system. Once inside, the cybercriminal leveraged IBM Aspera, a high-speed file transfer tool, to exfiltrate approximately 400GB of compressed data.
The Role of “abyss0”
The breach became publicly known when a cybercriminal, using the alias "abyss0," advertised the stolen data for sale on October 31, 2024, via BreachForums, a notorious marketplace for cybercrime. The data was initially listed for $20,000 but was later reduced to $10,000.

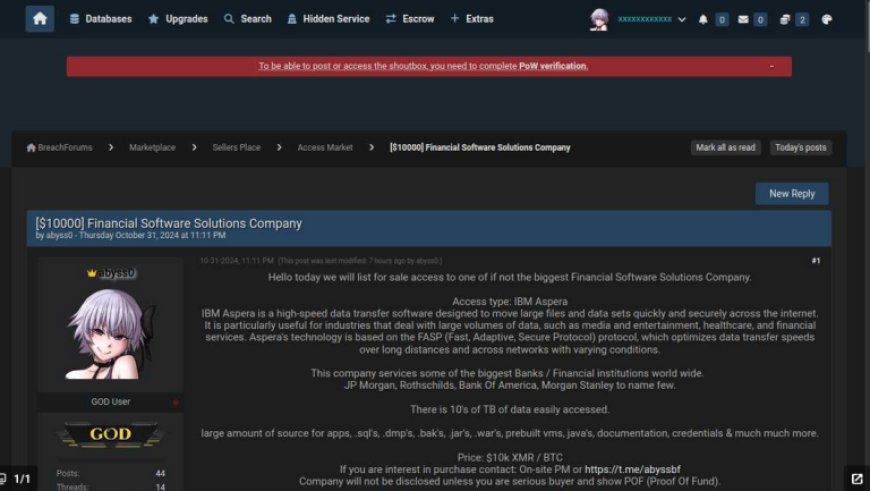
However, shortly after drawing attention, the seller vanished from both BreachForums and Telegram, where they had been advertising the stolen information. Cybersecurity experts speculate that "abyss0" either found a buyer for the data or went underground to avoid detection and scrutiny.
Scope of the Breach
While the full extent of the data breach is still being investigated, early findings suggest that the stolen files include:
- Client Data: Sensitive banking information, transaction details, and financial records from major Finastra clients.
- Internal Documents: Confidential operational materials related to Finastra’s services and systems.
Finastra clarified that the attackers did not deploy malware or tamper with customer files during the breach. However, the unauthorized extraction of sensitive data raises serious concerns about client confidentiality and security.
Finastra’s Response
On November 8, Finastra informed its customers about the breach, disclosing that suspicious activity had been detected the previous day on its SFTP platform. The company assured clients that customer operations and systems remain unaffected and that an alternative secure file-sharing platform had been implemented to ensure business continuity.
“Our investigations indicate that credentials were compromised, and the attacker did not use malware or access files beyond the exfiltrated data,” read the company’s notice.
Finastra has been transparent with customers, actively sharing Indicators of Compromise (IOCs) and providing updates on the investigation. The company’s Chief Information Security Officer (CISO) has been engaging directly with clients’ security teams to assess the breach and its potential impact.
Analysis and eDiscovery Process
Finastra is currently conducting a detailed eDiscovery process to determine the specific clients and products affected by the breach. Initial findings indicate that not all Finastra customers use the compromised version of the SFTP platform. However, the company acknowledges that the investigation is time-intensive due to the size and complexity of its customer base.
“For any customers who are deemed to be affected, we will be reaching out and working with them directly,” the company stated.
A History of Cybersecurity Challenges
This breach is not the first cybersecurity challenge Finastra has faced. In March 2020, the company suffered a ransomware attack that disrupted several core business operations for days. Finastra successfully recovered from the incident without paying a ransom, demonstrating resilience in the face of cyber threats.
Timeline of Events
- March 2023: Finastra’s client file transfer platform is allegedly infiltrated by the cybercriminal alias "abyss0."
- October 31, 2024: "abyss0" advertises stolen data on BreachForums, initially priced at $20,000.
- November 3, 2024: The price is reduced to $10,000.
- November 7, 2024: Finastra detects suspicious activity on its SFTP platform.
- November 8, 2024: Finastra notifies customers about the breach and shares preliminary findings.
- November 16, 2024: The cybercriminal "abyss0" vanishes, with accounts deleted from BreachForums and Telegram.
Concerns Over Cybercrime
This breach underscores the persistent threat posed by cybercriminals targeting critical financial systems. The apparent sophistication of the attack—using stolen credentials and high-speed file transfer tools—highlights the need for robust security measures.
While Finastra is working diligently to assess and mitigate the impact, the incident serves as a wake-up call for the financial industry to strengthen its cybersecurity defenses.
What's Your Reaction?
 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0